SAP- SECURITY
SAP Security/GRC Modules are Sub-Modules of SAP BASIS Module. Security Module deals with Permissions, Authorizations etc., aspects of System Admn., Functionality in an SAP Project. BASIS Consultants who are assigned with SECURITY responsibility in an SAP Project will learn “Exclusive SECURITY” Module focused mainly on SECURITY related Functions. As with BASIS Module, SECURITY Module can be learned by people from all Academic streams and become SECURITY Consultant.

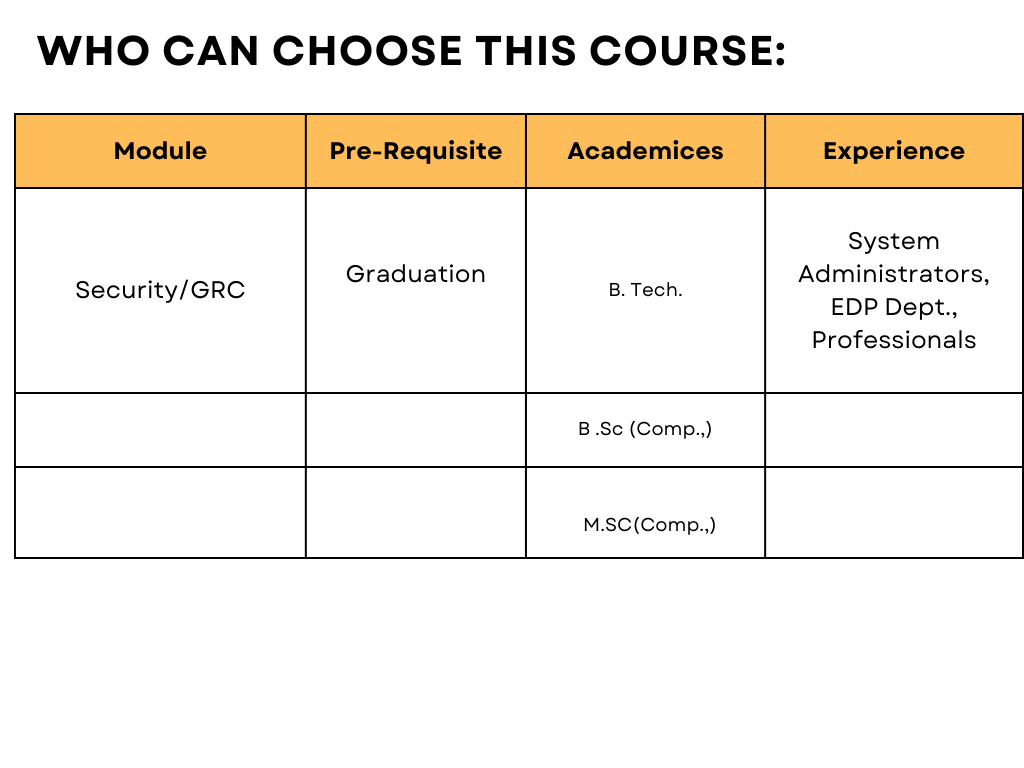
Eligibility for a course typically depends on the following:
- Prerequisites: Required prior courses or skills.
- Level of Study: Undergraduate, graduate, or continuing education.
- Program Requirements: Specific to your major or program.
- Open Enrollment: Available to all students as an elective.
- Special Permissions: Might need instructor or department approval.
- Availability: Limited seats may give priority to certain students.
- Location/Delivery: Online or specific campus availability.
Check the course catalog or consult with an academic advisor for specifics.
SAP - SECURITY COURSE CONTENT
• Overview of SAP-HR, SRM Security
• Org. chart assignments in SRM Assignments
• Indirect assignment of standard HR Roles to Organizational Objects
11) Overview of the GRC:
• Overview of SOX-SOD
• Classification of SOX Rules
• Introduction to GRC AC 10
